Steps to configure an IPSEC site to site VPN on a Cisco IOS device (GNS3 Lab)

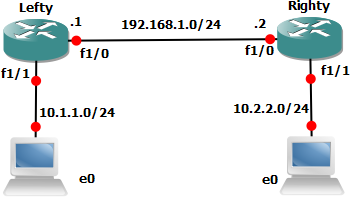
Just some short notes on basic IOS vpns using the topology below as an example. All the configuration examples are for the router Lefty. Grab the GNS3 .net file and initial configs [HERE] if you want to try.
The following five steps need to configured in order to create an IPSEC VPN on a Cisco IOS device.
| Desciption | |
| Step 1. | ISAKMP policy - Configure what parameters will be used for the IKE phase 1 tunnel |
| Step 2. | Transform Set – Configure what parameters will eb used for the IKE phase 2 tunnel (aka the IPSEC tunnel) |
| Step 3. | ACL – Create an ACL to define what "interesting" traffic will be sent over the VPN |
| Step 4. | Cypto Map – Configured using the previous parameters. |
| Step 5. | Apply – Apply the cypto map to an interface |
Step 1. - ISAKMP
Lefty#conf t
Lefty(config)#crypto isakmp enable
Lefty(config)#crypto isakmp policy 10
Lefty(config-isakmp)#authentication pre-share
Lefty(config-isakmp)#hash sha
Lefty(config-isakmp)#encryption aes 256
Lefty(config-isakmp)#group 5
Lefty(config-isakmp)#lifetime 3600
Lefty(config-isakmp)#exit
Lefty(config)#crypto isakmp key 0 SuperS3cure address 192.168.1.2
Lefty(config)#crypto isakmp keepalive 10 2 periodic
Lefty(config)#^Z
First of we enter config mode then enable isakmp, although by default it is enabled this probably wont be needed. The policy number is quite important. When the router tries to negotiate an acceptable phase one policy it always starts with the policy closest to 1 then work up in order until a negotiation is successful (using 10 leaves some room for growth if needed)
Now we configure the authentication method. Acceptable options are pre-shared key, RSA-Sig and RSA-Encr. For simplicity we'll use PSK at the moment. I'll do another post soon to explain the other options.
Next is the hash method to be used. Options are MD5 and SHA-1 (SHA-1 is the default)
Now we configure the encryption algorithm we want to use. In order of strength AES 256, AES 192, AES 128, 3DES, DES (DES as the default if nothing is explicitly configured)
Group <number> will configure the modulus size of the Diffie-Hellman key exchange. (Group 5 isnt supported on all versions of IOS!)
| Group | Description |
| 1 | The 768-bit Diffie-Hellman group. |
| 2 | The 1024-bit Diffie-Hellman group. |
| 5 | The 1536-bit Diffie-Hellman group. |
Lifetime is the time in seconds the Security Association (SA). 3600 = 1 hour (86400 (1 day) is the default)
Since we configured pre-shared key we need to configure the key on a per host basis in main config mode.
Just to emphasize dead peer detection (DPD) we set it to send keepalives every 10s then every 2s if a keepalive fails. Sent on demand rather than periodically like we have configured is the default.
Verify configuration with show crypto isakmp policy
Step 2. - Transform Set
Lefty#conf t
Lefty(config)#crypto ipsec transform-set MYTSETNAME esp-aes 256 esp-sha-hmac
Lefty(cfg-crypto-trans)#mode tunnel
Lefty(cfg-crypto-trans)#^Z
We configure IPSEC tunnel mode using 256 bit AES ecryption and sha-1 hmac.
Various other options are
Lefty(config)#crypto ipsec transform-set MYTSETNAME ?
ah-md5-hmac AH-HMAC-MD5 transform
ah-sha-hmac AH-HMAC-SHA transform
comp-lzs IP Compression using the LZS compression algorithm
esp-3des ESP transform using 3DES(EDE) cipher (168 bits)
esp-aes ESP transform using AES cipher
esp-des ESP transform using DES cipher (56 bits)
esp-md5-hmac ESP transform using HMAC-MD5 auth
esp-null ESP transform w/o cipher
esp-seal ESP transform using SEAL cipher (160 bits)
esp-sha-hmac ESP transform using HMAC-SHA auth
Verify with show crypto ipsec transform-set
Step 3. - ACL
Lefty#conf t
Lefty(config)#access-list 101 permit ip 10.1.1.0 0.0.0.255 10.2.2.0 0.0.0.255
Stright forward extended ACL config to define the "interesting" traffic that will be secured via the VPN.
Step 4. - Crypto Map
Lefty#conf t
Lefty(config)#crypto map LEFTY_TO_RIGHTY 10 ipsec-isakmp
% NOTE: This new crypto map will remain disabled until a peer
and a valid access list have been configured.
Lefty(config-crypto-map)#set peer 192.168.1.2
Lefty(config-crypto-map)#match address 101
Lefty(config-crypto-map)#set transform-set MYTSETNAME
Lefty(config-crypto-map)#^Z
We configure the IP or hostname of the opposite end of the tunnel. Configure the "interesting" traffic with the match command then finally configure the transform set to be used.
Verify with show crypto map
Step 5. - Apply
Lefty#conf t
Lefty(config)#int fastEthernet 1/0
Lefty(config-if)#crypto map LEFTY_TO_RIGHTY
Lefty(config)#ip route 10.2.2.0 255.255.255.0 192.168.1.2
Lefty(config)#^Z
Apply the configured crypto map to the outgoing interface. We need the static route to point to the router at the other end of the VPN tunnel.
Testing/Verify
The easest way to test is by using and extended ping. So here we use the 10.1.1.1 (fa 1/1) interface on Lefty as the source to ping the 10.2.2.2 address on the Righty router.
Lefty#p
Protocol [ip]:
Target IP address: 10.2.2.2
Repeat count [5]:
Datagram size [100]:
Timeout in seconds [2]:
Extended commands [n]: y
Source address or interface: 10.1.1.1
Type of service [0]:
Set DF bit in IP header? [no]:
Validate reply data? [no]:
Data pattern [0xABCD]:
Loose, Strict, Record, Timestamp, Verbose[none]:
Sweep range of sizes [n]:
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.2.2.2, timeout is 2 seconds:
Packet sent with a source address of 10.1.1.1
.!!!!
Success rate is 80 percent (4/5), round-trip min/avg/max = 4/5/8 ms
Now the ping has setup the VPN because of its "interesting" traffic (the first ping is lost in the VPN creation). We can verify with show crypto engine connections active
Lefty#show crypto engine connections active
Crypto Engine Connections
ID Interface Type Algorithm Encrypt Decrypt IP-Address
1 Fa0/0 IPsec AES256+SHA 0 4 192.168.1.1
2 Fa0/0 IPsec AES256+SHA 4 0 192.168.1.1
1001 Fa0/0 IKE SHA+AES256 0 0 192.168.1.1
You can see we have one IKE connection and an IPSEC tunnel for each direction.
m00nie :)
