Simple Zone Based IOS Firewall (GNS3 Lab)

Just a post about the basic config and options of Cisco IOS zone based firewall using the Topology below Grab the initial configs and GNS3 .net file [HERE]. From the initial configs all interfaces have connectivity to each other.
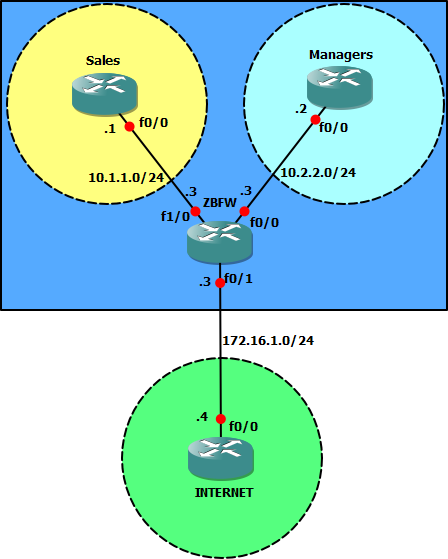
First off lets configure the zones and assign each interface to a zone.
ZBFW#conf t
ZBFW(config)#zone security ZONE_SALES
ZBFW(config-sec-zone)#exit
ZBFW(config)#zone security ZONE_MANAGERS
ZBFW(config-sec-zone)#exit
ZBFW(config)#zone security ZONE_INTERNET
ZBFW(config-sec-zone)#exit
ZBFW(config)#int fa 1/0
ZBFW(config-if)#zone-member security ZONE_SALES
ZBFW(config-if)#exit
ZBFW(config)#int fa 0/0
ZBFW(config-if)#zone-member security ZONE_MANAGERS
ZBFW(config-if)#exit
ZBFW(config)#int fa 0/1
ZBFW(config-if)#zone-member security ZONE_INTERNET
ZBFW(config-if)#^Z
ZBFW#
The default policy between zones is drop all if two interfaces are assigned to the same zone all traffic will be allowed. The only exception to the default deny all is the self zone. This is a special zone reserved for traffic destined to or sourced from the management plane of the device itself. Each interface can only be a member of one zone at a time.
So now there's no connectivity between the various zones. Lets configure the first zone pair. The Sales zone should only be allowed http access to the internet zone.
ZBFW#conf t
ZBFW(config)#class-map type inspect match-any CLASS_HTTP
ZBFW(config-cmap)#match protocol http
ZBFW(config-cmap)#exit
ZBFW(config)#policy-map type inspect POLICY_HTTP
ZBFW(config-pmap)#class type inspect CLASS_HTTP
ZBFW(config-pmap-c)#inspect
ZBFW(config-pmap-c)#exit
ZBFW(config-pmap)#exit
ZBFW(config)#zone-pair security ZP_SALES_INTERNET source ZONE_SALES destination ZONE_INTERNET
ZBFW(config-sec-zone-pair)#service-policy type inspect POLICY_HTTP
ZBFW(config-sec-zone-pair)#^Z
ZBFW#
As you can see above its very similar to the "modular" cli to configure qos etc.
- Define a class map. This should match all the traffic you want to apply the policy to. Can be either a protocol or an ACL.
- Configure a policy map to use the class map and applys some action to it e.g allow, deny or inspect.
- Apply the policy map to a zone pair.
From the config above we configured a class map called CLASS_HTTP to match the http protocol. The Policy map POLICY_HTTP uses this class map and anything matching the class map will be inspected (auto allows the return traffic). Finally we define a zone pair called ZP_SALES_INTERNET with the sales zone as the source and the internet zone as the destination.
Now we can test that the sales zone has http access to the internet (telnet 4.4.4.4 80) but all other traffic its dropped (telnet, ICMP and ssh) including access from sales to managers zone. A zone pair just defines what access it allowed from one zone to another. Its only defines traffic in one direction (although inspect can we used to auto allow return traffic).
The Manager zone should be allowed ssh, telnet and http access to the internet zone (ICMP should be blocked).
ZBFW(config)#class-map type inspect match-any CLASS_STH
ZBFW(config-cmap)#match class-map CLASS_HTTP
ZBFW(config-cmap)#match protocol ssh
ZBFW(config-cmap)#match protocol telnet
ZBFW(config-cmap)#exit
ZBFW(config)#policy-map type inspect POLICY_STH
ZBFW(config-pmap)#class type inspect CLASS_STH
ZBFW(config-pmap-c)#inspect
ZBFW(config-pmap-c)#exit
ZBFW(config-pmap)#exit
ZBFW(config)#zone-pair security ZP_MANAGERS_TO_INTERNET source ZONE_MANAGERS destination ZONE_INTERNET
ZBFW(config-sec-zone-pair)#service-policy type inspect POLICY_STH
ZBFW(config-sec-zone-pair)#^Z
ZBFW#
Here we configure the class map CLASS_STH to match the protocols ssh and telnet. Its also possible to match class maps within class maps like CLASS_HTTP is above. Then we again configure a policy map to inspect traffic matched by the class map. Finally we configure a zone pair and assign the service policy.
Now we can test that from the managers router we have telnet, http and ssh access to the internet router. ICMP should still be dropped. All traffic between sales and managers zones should still be dropped.
Finally we want to configure remote management access to the ZBFW router from the management zone to only allow telnet.
ZBFW#conf t
ZBFW(config)#access-list 101 permit tcp 10.2.2.0 0.0.0.255 any eq telnet
ZBFW(config)#class-map type inspect match-all CLASS_SELF
ZBFW(config-cmap)#match access-group 101
ZBFW(config-cmap)#exit
ZBFW(config)#policy-map type inspect POLICY_SELF
ZBFW(config-pmap)#class type inspect CLASS_SELF
ZBFW(config-pmap-c)#inspect
%No specific protocol configured in class CLASS_SELF for inspection. All protocols will be inspected
ZBFW(config-pmap-c)#exit
ZBFW(config-pmap)#exit
ZBFW(config)#$ecurity ZP_MAN_TO_SELF source ZONE_MANAGERS destination self
ZBFW(config-sec-zone-pair)#service-policy type inspect POLICY_SELF
ZBFW(config-sec-zone-pair)#^Z
Now we can test that only telnet access from the management router to the ZBFW is the only access allowed. We can also run the following on the ZBFW router to check the hits/config of the zone pair.
ZBFW#show policy-map type inspect zone-pair ZP_MAN_TO_SELF
Zone-pair: ZP_MAN_TO_SELF
Service-policy inspect : POLICY_SELF
Class-map: CLASS_SELF (match-all)
Match: access-group 101
Inspect
Packet inspection statistics [process switch:fast switch]
tcp packets: [18:0]
Session creations since subsystem startup or last reset 1
Current session counts (estab/half-open/terminating) [0:0:0]
Maxever session counts (estab/half-open/terminating) [1:1:1]
Last session created 00:05:28
Last statistic reset never
Last session creation rate 0
Maxever session creation rate 1
Last half-open session total 0
Class-map: class-default (match-any)
Match: any
Drop (default action)
4 packets, 96 bytes
Now it be try to telnet from sales to ZBFW the connection is still allowed! Unlike communication between all other zones when the self zone is involved the default is to allow all unless explicitly denied.
As an extra configuration ip inspect log drop-pkt under the main configuration mode can log all packets dropped/denied by the firewall helping debugging and monitoring.
m00nie :)
