EAP, EAPOL and EAP types

Extensible Authentication Protocol (EAP) - is a transport mechanism used in 802.1x to authenticate supplicants (hosts/pcs) against a backend server (Radius) via an authenticator (Switch).
The first byte of the EAP header contains the code field, this identifies the EAP packet type. The four different codes are shown below. Any EAP packets that do not match on the the four codes are ignored.
| EAP Code | Type |
| 1 | Request |
| 2 | Response |
| 3 | Success |
| 4 | Failure |
EAP over LAN (EAPOL) - Is the encapsulation technique used for the authenticator and the supplicant to communicate with over the LAN ( including Ethernet and WLANs). The destination MAC address for the EAPOL header uses the Port Access Entity (PAE) group address of 01:80:c2:00:00:03.
Its is important to note that (on Cisco switches) when in an unauthorized state the switchport will only allow EAPOL, CDP and STP frames to pass.
Example of an EAP (OTP) process
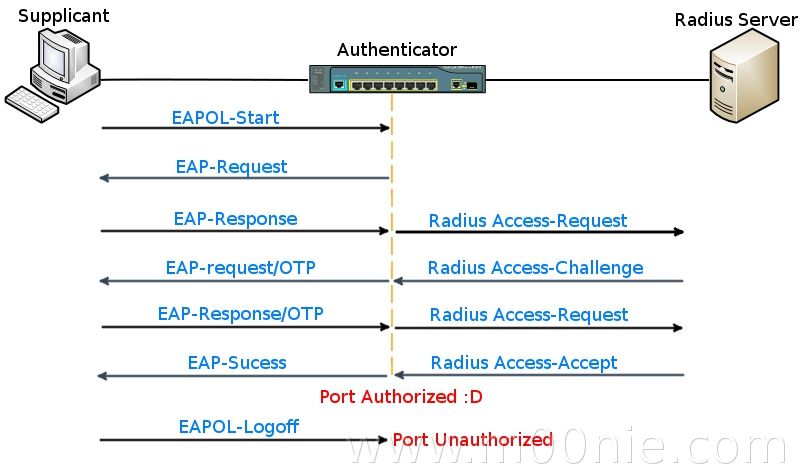
As you can see in the diagram the first frame sent is an EAPOL-Start frame. This frame is not critical and the process can be started by the authenticator sending the EAP-Request Frame.
Next the supplicant responds with an EAP-Response. Messages from the Authenticator to the Radius server use the radius protocol (UDP 1812 for Authentication)
When the authenticator receives an Access-Accept packet from the radius server it will authorize the port and allow access to the supplicant. If access is denied by the Radius server an Access-Reject message will be sent to the authenticator and the port will stay unauthorized.
The supplicant can terminate the authentication of the port by sending a EAPOL-logoff frame to the authenticator.
EAP Types
- EAP-MD5 - Uses Md5 hashes rather than plan text when transmitting over the network. The server sends the supplicant a secret which the supplicant then hashes using its password. The hash is then passed back to the server which does the same calculation and checks the output matches. This method requires the server to maintain the passwords in a format it can reverse to plain text.
- Cisco Lightweight EAP (LEAP) - This is an example of a mutual authentication protocol because the supplicant also authenticates the authentication server. Both the supplicant and the authentication server must share a secret this in then used to hash the passwords which can then be checked for matches.
- PEAP with MSCHAPv2 - Or protected EAP encapsulates the EAP method within a TLS tunnel for added security. The most common variation is Peap with MS-CHAPv2 in which the Radius server relays the MS-CHAP credentials (E.g Active Directory) to a Domain controller or similar to be validated.
- EAP-TLS - Utilizes transport layer security and again mutually authenticates both the server and the supplicant. No passwords are used though and this type relies purely on PKI certificates. This means that each supplicant must have its own certificate installed.
- EAP-TTLS - Stands for Tunnelled Transport Layer Security. This type can encapsulate non EAP authentications E.g. PPP & CHAP. It also doesnt require every supplicant to have its own certificate installed.
- EAP-Flexible Authenticaion via Secure Tunneling (EAP-FAST) - Uses a Protected Access Credential (PAC) to establish a TLS tunnel in which client credentials are verified. PACs can be setup manually or automatically although if these are captures there is a possible security issue.
Not definitive definitions but hopefully enough to distinguish between them. More detail can be found on the wikipedia EAP article.
m00nie :)
