Dynamic point to point IPSEC VPN tunnels using DTVIs (GNS3 Lab)

Manually configuring point to point IPSEC tunnels can become a big administrative burden as the number of endpoints grows. In a hub and spoke environment we can use Dynamic Virtual Tunnel Interfaces (DVTI) to help ease this burden of lots of site to site or remote access tunnels
When using DVTIs virtual access interfaces are dynamically created by using a configured template on the hub. When the interfaces are created dynamically from the template they are called virtual access interfaces rather than virtual tunnel interfaces. The template can include normal interface features like ACLs, Netflow,IOS firewall settings and QoS which are then applied to the dynamically created access interface. The configuration of the spokes is just uses the "normal" static VTI config.
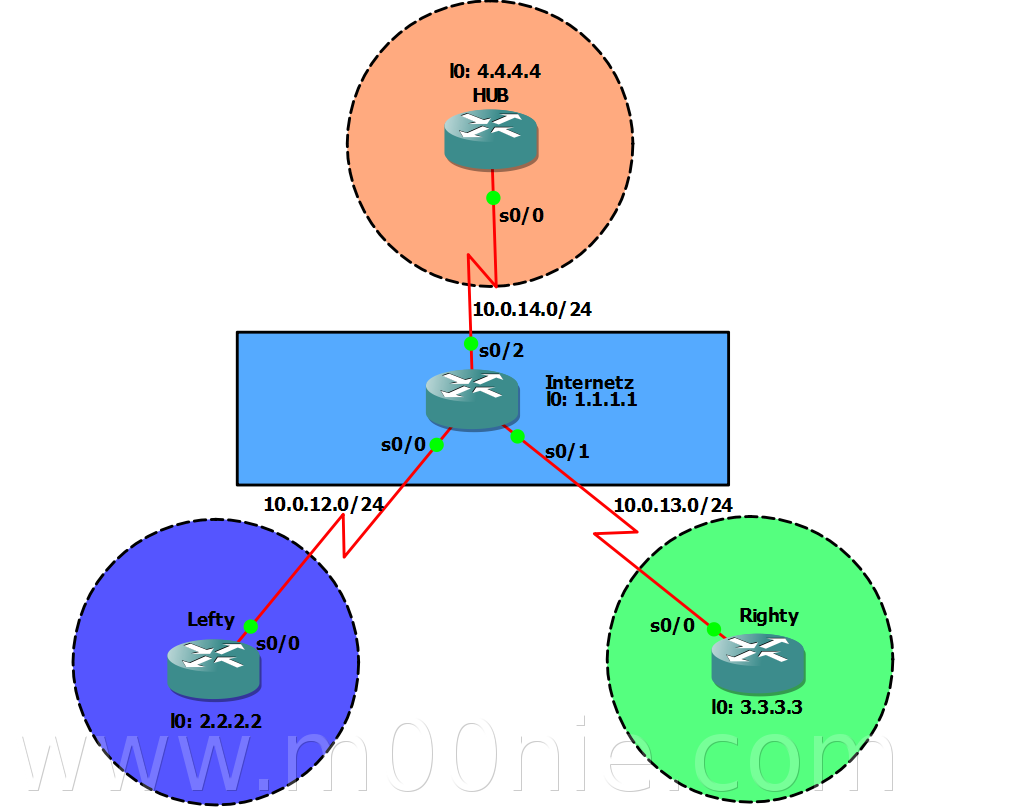
We will use the topology above and the initial .net file can be grabbed which includes all interfaces addressed and basic connectivity [here]
The hub
The steps below outline the configuration needing done on the hub device
| Step | Description |
| 1 | ISAKMP + Key |
| 2 | Transform set |
| 3 | IPSEC protection profile |
| 4 | Virtual template interface (VTI) |
| 5 | ISAKMP profile to map peeps to VTI |
1. ISAKMP + Key
The first task to configure on the hub device is to create pre-shared keys and a better than default ISAKMP policy. Righty will have its own key and Lefty will have a common key.
HUB#conf t
Enter configuration commands, one per line. End with CNTL/Z.
HUB(config)#crypto isakmp policy 100
HUB(config-isakmp)#authentication pre-share
HUB(config-isakmp)#hash sha
HUB(config-isakmp)#encryption aes 128
HUB(config-isakmp)#lifetime 7200
HUB(config-isakmp)#group 5
HUB(config)#crypto keyring MyVpnKeyring
HUB(conf-keyring)#pre-shared-key address 10.0.13.3 key s00perS3creTKee2
HUB(conf-keyring)#pre-shared-key address 0.0.0.0 0.0.0.0 key s00perS3creTKee1
2. Transform Set
There are default transform sets in newer IOS versions but I find it clearer to define my own so this step can be optional. The name of the transform set will be AES_128-SHA and will use AES 128 and SHA-1 in tunnel mode. Verify config with show crypto ipsec transform-set
HUB#conf t
Enter configuration commands, one per line. End with CNTL/Z.
HUB(config)#crypto ipsec transform-set AES_128-SHA esp-aes 128 ah-sha-hmac
HUB(cfg-crypto-trans)#mode tunnel
3. IPSEC protection profile
This profile defines the protection policy for the VTI tunnel. We configure a protection profile called MyIPSECProtectionProfile and configure it to use the transform set from step 2. We then configure the use of Perfect Forward Secrecy (PSF) (the default is not to negotiate this but im paranoid) and configure a SA lifetime of 2 hours (default is 1 hour). Verify with show crypto ipsec profile
HUB#conf t
Enter configuration commands, one per line. End with CNTL/Z.
HUB(config)#crypto ipsec profile MyIPSECProtectionProfile
HUB(ipsec-profile)#description This is mt IPSEC PP :)
HUB(ipsec-profile)#set transform-set AES_128-SHA
HUB(ipsec-profile)#set pfs group5
HUB(ipsec-profile)#set security-association lifetime seconds 7200
4. Virtual template interface
Now we create the virtual template that all DVTI will be derived from. As you can see we use the IPSEC protection profile configured in step 3.
HUB#conf t
Enter configuration commands, one per line. End with CNTL/Z.
HUB(config)#interface virtual-template 1 type tunnel
HUB(config-if)#ip unnumbered s 0/0
HUB(config-if)#tunnel mode ipsec ipv4
HUB(config-if)#tunnel protection ipsec profile MyIPSECProtectionProfile
5. ISAKMP map
The final step on the HUB router is to configure the ISAKMP profile that will match peers to the new virtual template. We configure the two VPN spokes and the use of the keyring.
HUB#conf t
Enter configuration commands, one per line. End with CNTL/Z.
HUB(config)#crypto isakmp profile ISAKMPProfile
% A profile is deemed incomplete until it has match identity statements
HUB(conf-isa-prof)#match identity address 10.0.12.2 255.255.255.255
HUB(conf-isa-prof)#match identity address 10.0.13.3 255.255.255.255
HUB(conf-isa-prof)#keyring MyVpnKeyring
HUB(conf-isa-prof)#virtual-template 1
All done for the hub :)
Spokes
We will use the steps below to configure the spoke devices. This config is exactly the same on the spoke devices for static site to site VTI VPNs.
| Step | Description |
| 1 | IKE Policy |
| 2 | Transform set |
| 3 | IPSEC Protection profile |
| 4 | VTI |
1. IKE
From version 12.4(20)T there are 8 default IKE policies so this step can be optional. Verify with show crypto isakmp policy
Lefty#conf t
Enter configuration commands, one per line. End with CNTL/Z.
Lefty(config)#crypto isakmp policy 100
Lefty(config-isakmp)#authentication pre-share
Lefty(config-isakmp)#hash sha
Lefty(config-isakmp)#encryption aes 128
Lefty(config-isakmp)#lifetime 7200
Lefty(config-isakmp)#group 5
Lefty(config-isakmp)#exit
Lefty(config)#crypto isakmp key 0 s00perS3creTKee1 address 10.0.14.4
2. Transform Set
Again from version 12.4(20)T default transform sets were included so this is an optional step.
Lefty#conf t
Enter configuration commands, one per line. End with CNTL/Z.
Lefty(config)#crypto ipsec transform-set AES_128-SHA esp-aes 128 ah-sha-hmac
Lefty(cfg-crypto-trans)#mode tunnel
3. IPSEC Protection profile
Now to create the protection profile.
Lefty#conf t
Enter configuration commands, one per line. End with CNTL/Z.
Lefty(config)#crypto ipsec profile MyIPSECProtectionProfile
Lefty(ipsec-profile)#description This is mt IPSEC PP :)
Lefty(ipsec-profile)#set transform-set AES_128-SHA
Lefty(ipsec-profile)#set pfs group5
Lefty(ipsec-profile)#set security-association lifetime seconds 7200
4. VTI
Now we create a new IP addressed tunnel interface (can be unnumbered if required)
Lefty#conf t
Enter configuration commands, one per line. End with CNTL/Z.
Lefty(config)#int tunnel 0
Lefty(config-if)#ip unnumbered s 0/0
Lefty(config-if)#tunnel source s 0/0
Lefty(config-if)#tunnel destination 10.0.14.4
Now when you check your ipsec/isakmp tunnels should be built :) Config of righty is very similar to lefty and no extra config needs to be done on the HUB!
m00nie :D
